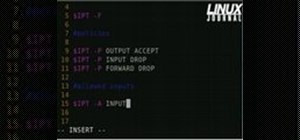
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.











2 Comments
getting ajax error adding comment so gonna split that on few comments... sorry for that
First of all thanks a lot for the great articles and tutorials. I really love this site and have more confidence to this site than others.
1) Separated Pages, How to Make a Book?
The problem is that many things can be a bit difficult for the beginners as their knowledge can look like a thousands separated pages and probably far away to close everything in just one book. You give another pages and what I like in very friendly way but what if you could help to merge that knowledge?
2) Bump with the Wall After 15 Years
15 years ago I started learn programming and had similar feeling as now after I spent years coding, coding and coding. Now I don't need ready solutions (ok maybe sometimes) because I always see how I can solve the same thing on thousands way but I remember how hard was in the past when was asking silly questions being ignore sometimes by more experienced guys.
3) Try, Do Mistakes.. Don't Expect Ready Solution..
Now learn again how to walk by reading about security, anonymity, etc. Many guys give nice tutorials, suggestions and most of the solutions work as a charm but how to merge everything together? They say there is no such way cos everyone has to find own way... yes that's true... I agree and probably some day will find own way but now I really need ready solution to could start from something and probably not only me.
4) IP, DNS, Mac, What Else?
Have read hundreds websites about IPTABLES. Some of them were very simple and base so have to spend few weeks to finally build something nice but then how to use it with two interfaces, how to use it with VPN... ok success... then TOR, DNSmasq, dnscrypt-proxy, privoxy, clamav, havp, auto macchanger, proxychain, polipo... how the hell to start everything on boot... I installed many distributions and configured better or worse configurations... great... I learned... for sure... but did I make it good? probably not if I still get some errors... would anyone be able to create ONE tutorial how to configure system ready to use? where I don't need to worry much about my IP, DNS leak, my Mac, MiM, Viruses, Rough Hotspot, DNS poisoning, etc. etc.
5) Solution for Solution
I found good article to make something like below:
Request -> VPN -> IPTABLES -> HAVP -> PRIVOXY -> DNSmasq -> Web server -> Privoxy -> ClamAV -> HAVP -> IPTABLES -> VPN -> Response
It sounds ok to me but now I use dnscrypt-proxy which as I know is not needed in this configuration, what about polipo, how to use Tor with this but VPN over Tor and use only if I need... having that do I still need a proxychain? what about my MAC? how to make it work with psad and fwsnort... did I miss anything?
6) Just One Tutorial from Tutorials
Can you create one good tutorial to build something like that or even better? My knowledge is not enough to suggest anything but something wants me to believe that hackers do not stop just on VPN and DNSmasq. I was experimenting with below:
| VPN | TOR | IPTABLES | PSAD | FWSNORT | CLAMAV | HAVP | DNSMASQ | DNSCRYPT-PROXY | PRIVOXY | POLIPO | AUTO MACCHANGER | PROXYCHAIN |
I know that some from above cannot work together but that's my main problem... which one should be run together and which may create the best configuration or what else should be added to give 99,9% bulletproof system. I would be very thankful for such tutorial.
Share Your Thoughts