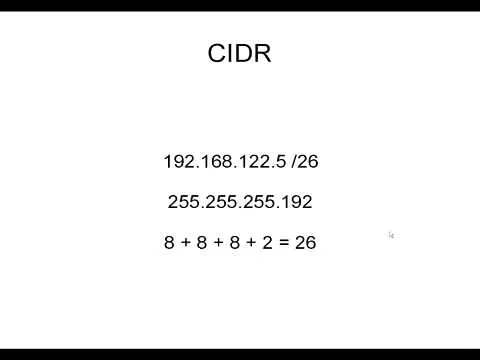
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then type "airodump-ng -c (channel) - w (filename) --bssid (MAC address) wlan0" and press enter. It will now scan the network and collect info. Now you need to open up a second console window. In this window type " airplay-ng -0 5 -c (Station MAC) -a (BSSID MAC) wlan0" and press enter. This will try to de-authenticate the current user from the network so they will have to re-sign on and re-send their WPA key. You can now close the second window. Go back to the first window. The top line should say "WPA handshake". this shows that you were successful. Now press Control-C. Type "DLR". This will show you all the file of the directory. You are looking for the "password" file you created earlier. Type "aircrack-ng password-06.cap -w /pentest/wireless/aircrack-ng/test/password.lst" (NOTE: you must type in the most recent password file info) and press enter to search for the password. (Keep in mind, you may need to search for additional password lists online and paste them in the password folder on your computer.) Congratulation, you've done it!
Apple's iOS 26 and iPadOS 26 updates are packed with new features, and you can try them before almost everyone else. First, check Gadget Hacks' list of supported iPhone and iPad models, then follow the step-by-step guide to install the iOS/iPadOS 26 beta — no paid developer account required.




















Comments
Be the first, drop a comment!