Trending about Computer Networking

how to
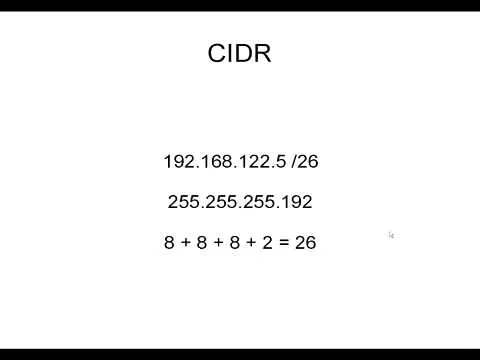
How to Subnet Using CIDR Notation

forum
Ok Sorry I Posted This Worng Help Cracking Rdp

forum
Ok So I Have a Couple of Comps or Servers with the Rdp Port Open However There All Have a Sonic Wall Which Denys and Con



























Featured On WonderHowTo:
Productivity & Shortcuts






Featured On WonderHowTo:
Music & Audio







Featured On WonderHowTo:
Augmented Reality








Featured On WonderHowTo:
Gaming