How-To Guides about Computer Networking

how to
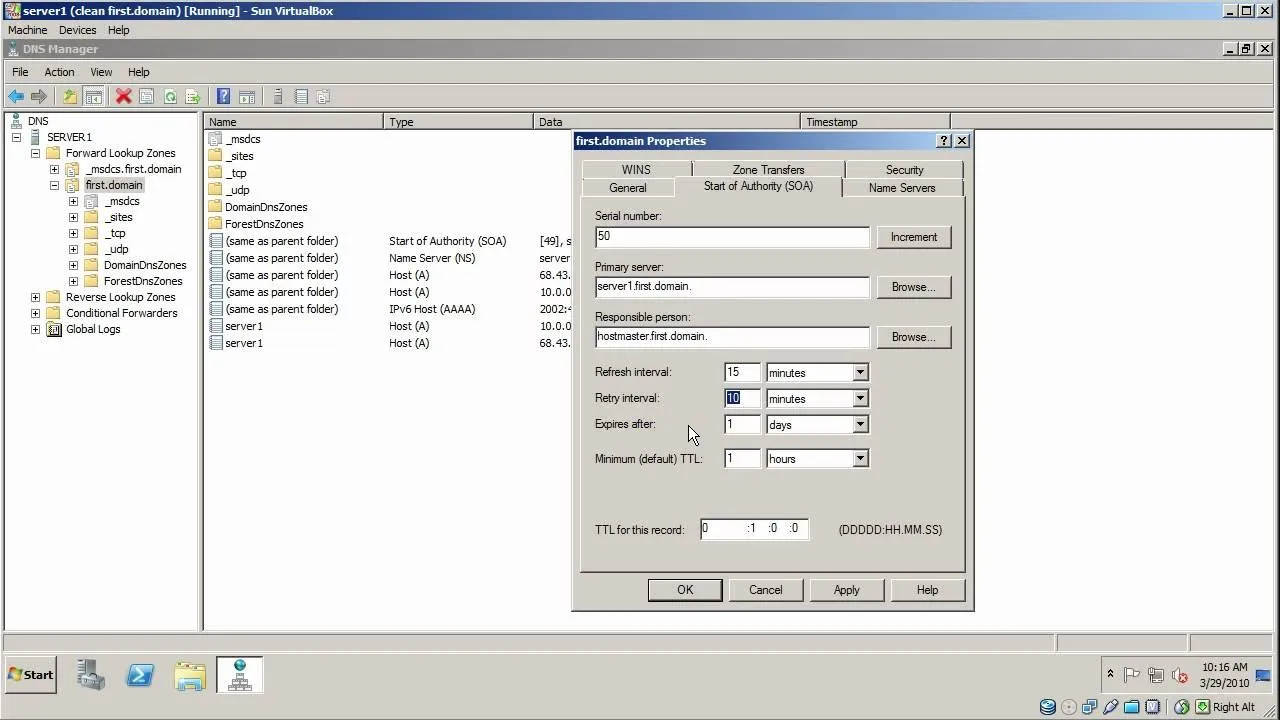
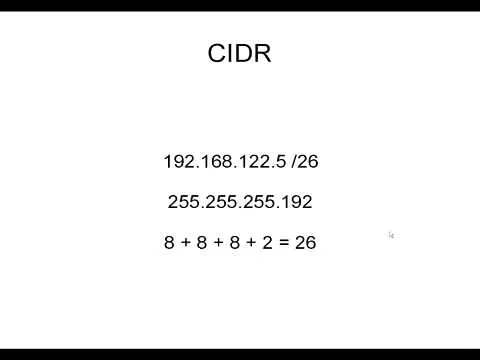
How to Subnet Using CIDR Notation

how to
How to Setup an Asterisk Server

how to
How to Tips for Selecting Ecommerce Web Design Company





















Featured On WonderHowTo:
Productivity & Shortcuts






Featured On WonderHowTo:
Music & Audio









Featured On WonderHowTo:
Augmented Reality








Featured On WonderHowTo:
Gaming